Cybersecurity researchers from UC Irvine and Tsinghua University have unveiled a potent cache poisoning attack called "MaginotDNS," designed to target Conditional DNS (CDNS) resolvers. This sophisticated attack has the potential to compromise entire top-level domains (TLDs) and exploit vulnerabilities within DNS software and server modes.
Introduction to MaginotDNS Attack
The MaginotDNS attack capitalizes on inconsistencies in security checks among various DNS software and server modes, leaving approximately one-third of all CDNS servers susceptible. This attack exposes a critical vulnerability that could have significant implications for the integrity of DNS resolution.
The Vulnerability in CDNS Resolvers
The MaginotDNS attack has a significant impact on CDNS resolvers, affecting both recursive and forwarding query modes, which are employed by ISPs and enterprises to reduce costs and enhance access control.
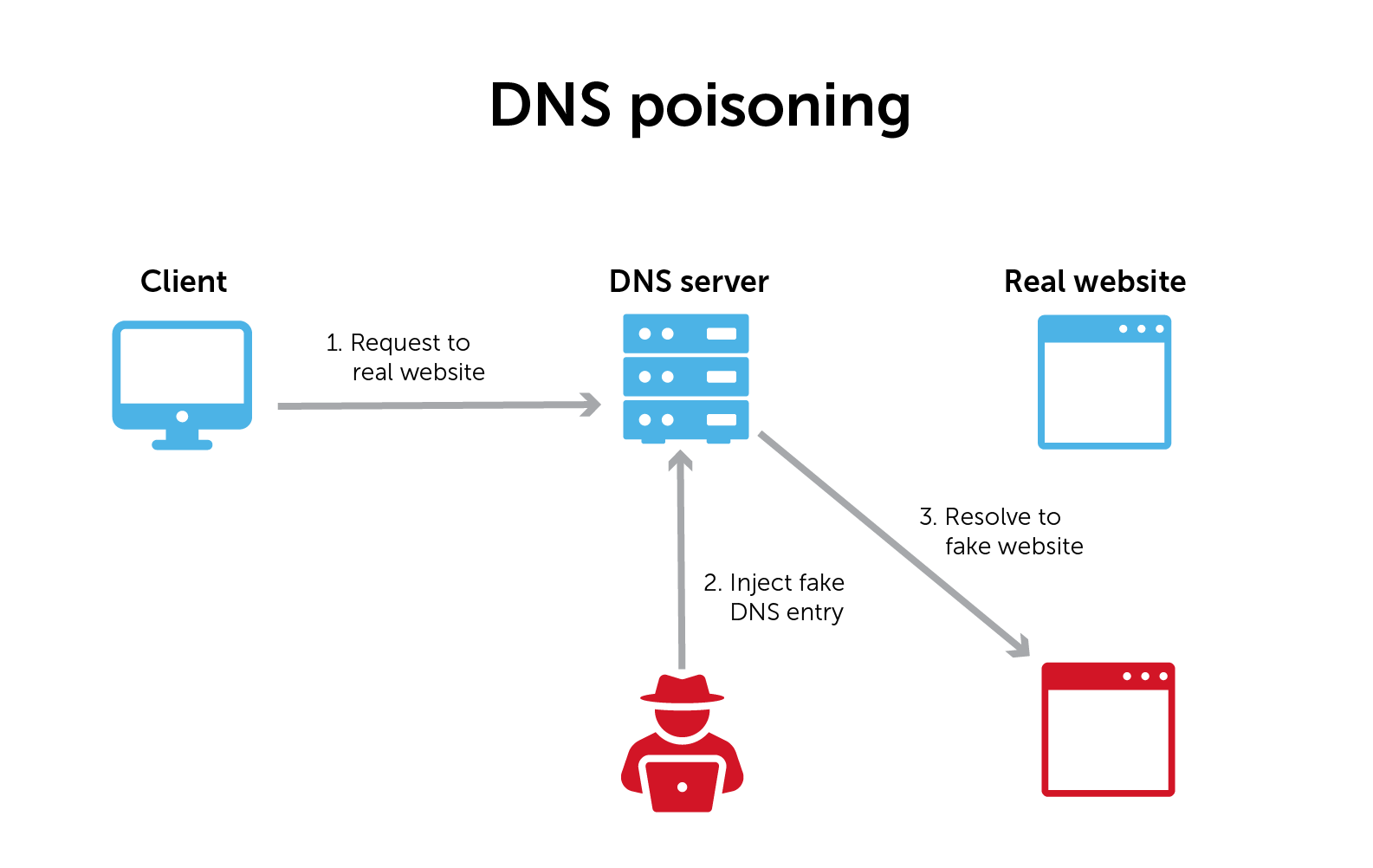
Understanding DNS Cache Poisoning
DNS (Domain Name System) plays a crucial role in converting human-readable domain names into numerical IP addresses, facilitating network connections. DNS cache poisoning involves injecting forged responses into a DNS resolver's cache, leading users to incorrect IP addresses and potentially malicious websites.
Evolution of DNS Cache Poisoning Attacks
The history of DNS cache poisoning includes notable attacks such as the Kashpureff Attack in 1997 and the Kaminsky Attack in 2008. These attacks exploited weaknesses in DNS protocols to redirect users to malicious sites.
The Role of Bailiwick Checks
The researchers found that while bailiwick checks are effectively implemented in the recursive mode of CDNS resolvers, the forwarding mode remains vulnerable. This vulnerability allows attackers to exploit the forwarding mode's weaknesses and compromise the integrity of the DNS cache.
Inconsistencies in DNS Software
Disparities in bailiwick checking were identified across prominent DNS software, including BIND9, Knot Resolver, Microsoft DNS, and Technitium. Certain configurations treated all records as under the root domain, rendering them highly vulnerable.
On-Path and Off-Path Attacks
The MaginotDNS attack encompasses both on-path and off-path attack scenarios. The off-path attack, although more complex, offers higher value to threat actors. Off-path attacks involve predicting the source port and transaction ID of the target's recursive DNS server to send forged responses from a malicious DNS server.
Countermeasures and Mitigations
The researchers conducted a comprehensive scan of the internet, identifying vulnerable CDNS resolvers. They found that a significant number of CDNS servers were susceptible to both on-path and off-path attacks. Vendors like Microsoft and others have acknowledged and resolved the vulnerabilities, issuing patches and guidelines for administrators.
Conclusion
The MaginotDNS attack underscores the importance of continuous vigilance in securing DNS infrastructure. With vulnerabilities identified and patched, the DNS community can work collectively to strengthen defenses against cache poisoning attacks and ensure the integrity of internet resources.
By highlighting the intricate workings of the MaginotDNS attack, researchers have shed light on the evolving landscape of cybersecurity threats, emphasizing the need for robust safeguards in DNS technologies.
I hope this article helped you, please share as it really helps us.
Leave a Reply